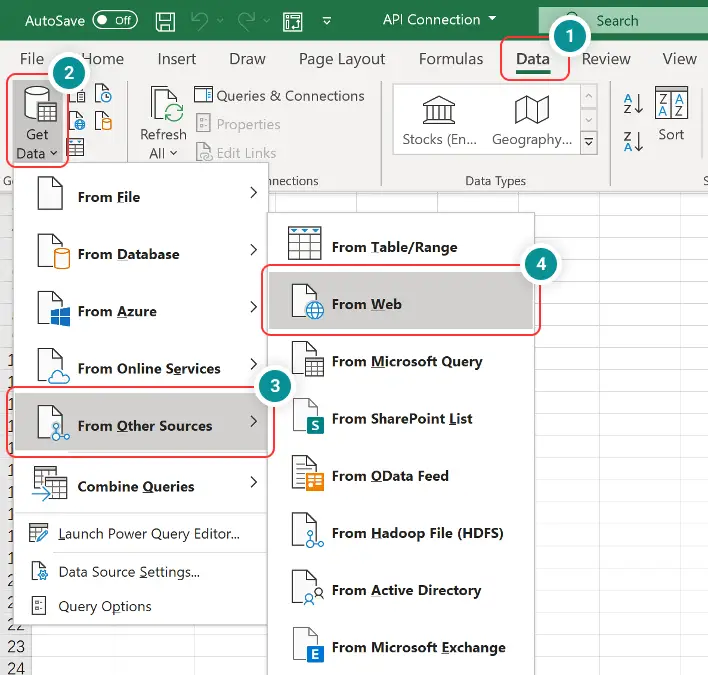
How to Create a Secure JSON API for Your Spreadsheet Data. Learn how to create a secure JSON API for your spreadsheet data with easy steps. Simplify your data sharing today!
<<<<< Buy Now from Official offer >>>>>
Introduction to JSON APIs & Spreadsheet Data Security
Creating a JSON API for spreadsheet data can be a useful tool. It allows sharing data effectively while ensuring security. JSON stands for JavaScript Object Notation. It is a lightweight data format. It is easy to read & write for humans & machines.
Spreadsheet data often contains sensitive information. This includes personal & financial details. It is vital to protect this data. A secure JSON API can help. It enables safe communication between applications. Users can access their data without compromising security.
In my experience, I created a JSON API for a client using Google Sheets. They needed a way to present data securely to users. I found the process rewarding & insightful. It made me appreciate the importance of data security in application development.
Essential Steps to Create a Secure JSON API
To build a secure JSON API, follow these steps:
1. Determine Your Requirements
– Identify the data you want to expose.
– Consider user roles & permissions.
2. Choose Your Technology Stack
– Select a programming language for your API.
– Common languages include Python & Node.js.
3. Set Up Your Environment
– Create a development environment.
– Use tools like Postman for testing.
4. Build the API Endpoint
– Create endpoint routes.
– Use frameworks like Flask or Express.
5. Implement Security Measures
– Use HTTPS to encrypt data.
– Ensure proper authentication & authorization.
6. Test Your API
– Use tools to send requests to your API.
– Verify that sensitive data is protected.
Consider the challenges of each step. Carefully planning will enhance the security of your JSON API.
- Define user roles clearly.
- Implement authentication methods.
- Review API response formats.
Building a secure JSON API requires attention to detail. Make sure to review the code frequently during the development process.
Choosing the Right Technology for Your JSON API
Selecting the appropriate technology stack is crucial. A strong framework or library can simplify API development. Popular choices include:
| Technology | Advantages |
|---|---|
| Node.js | Fast & scalable for I/O tasks |
| Python (Flask/Django) | Easy to learn, versatile |
| Ruby on Rails | Convention over configuration |
| Java (Spring) | Strong for large applications |
Consider your team’s expertise. Choose a language & framework you can use comfortably.
Make sure to assess the library’s security features. Does it provide built-in options for securing APIs? This is a key consideration.
Setting Up Your Development Environment
Creating a development environment is an important step. It allows you to work efficiently. Here are the components to consider:
1. Code Editor
– Choose an editor that suits your workflow.
– Visual Studio Code & Sublime Text are popular options.
2. Version Control
– Use Git for tracking changes.
– Platforms like GitHub or GitLab can host your projects.
3. API Testing Tool
– Postman is a powerful tool for testing APIs.
– It helps in sending requests to endpoints easily.
4. Local Server
– Set up a local server to run your API.
– Tools like XAMPP or Node.js can be useful.
By preparing your environment, you increase productivity. It also reduces the chances of errors during development.
My local development setup included Node.js & Postman. This combination made it simple to test my API. I appreciated how easy it was to simulate requests & responses.
Creating Your JSON API Endpoint
Developing the API endpoint is the core part of the project. Follow these steps to ensure clarity & organization in your code:
1. Define Routes
– Decide on the HTTP methods you will use. Common methods include GET, POST, PUT, & DELETE.
2. Code Your Functions
– Write functions that handle each request type. Return the relevant data securely.
3. Data Handling
– Ensure your API processes data correctly. Use JSON format for requests & responses.
4. Response Structure
– Define a clear response structure. Include status codes to represent success or failure.
Here’s an example of a basic structure for an API in Node.js:
javascript
const express = require(‘express’);
const app = express();
app.get(‘/data’, (req, res) => {
res.json({message: “This is your data”});
});
app.listen(3000, () => {
console.log(“Server is running on port 3000”);
});
Make sure to test each endpoint thoroughly. Check responses for both valid & invalid requests. This helps to identify potential security gaps.
Implementing Security Measures
Security is the highest priority when creating a JSON API. Consider the following strategies:
1. Use HTTPS
– Always run your API over HTTPS.
– This encrypts the data transmitted over the network.
2. Authentication
– Implement authentication methods like OAuth.
– This provides access control for users.
3. Authorization
– Verify that users have permission to access data.
– Implement role-based access control to enhance security.
4. Rate Limiting
– Set limits on how often users can hit the API.
– This helps prevent abuse & protects server resources.
5. Input Validation
– Validate all input data to avoid SQL injection or other attacks.
By implementing these measures, you enhance the security of your JSON API. Always keep your dependencies up to date. Unpatched libraries can become vulnerabilities.
“Creating a secure API is crucial for protecting sensitive data.” – Jamie Collins
Testing Your JSON API for Security & Functionality
Testing is essential for ensuring the reliability of your API. Make sure to plan your tests effectively. Here are some testing types to consider:
1. Unit Testing
– Check individual parts of your API for correctness.
– Use frameworks like Mocha or Jest.
2. Integration Testing
– Test how different parts of the API work together.
– Tools like Postman can help automate this process.
3. Security Testing
– Conduct tests specifically for vulnerabilities.
– Tools like OWASP ZAP can assist with identifying risks.
4. User Acceptance Testing
– Involve real users to validate the API’s usability.
– Collect feedback & make improvements where necessary.
Always document your tests. Clear documentation helps in future development. It also aids in onboarding new team members.
| Testing Type | Description |
|---|---|
| Unit Testing | Validates single components of the API |
| Integration Testing | Checks the interaction between components |
| Security Testing | Identifies potential vulnerabilities |
| User Acceptance Testing | Validates API usability with real users |
By thoroughly testing your API, you can ensure both functionality & security. This proactive approach avoids issues post-launch.
Best Practices for Maintaining Your JSON API Security
Maintaining the security of your JSON API does not end with development. It is an ongoing process. Follow these best practices:
1. Regular Updates
– Keep your software libraries updated.
– Regular updates patch known vulnerabilities.
2. Logging
– Implement logging to monitor API access.
– Keep track of unusual or suspicious activity.
3. Documentation
– Maintain clear & concise API documentation.
– It should include security considerations for users.
4. Educate Your Team
– Hold training sessions on security best practices.
– Make sure everyone understands their role in security.
5. Backup Your Data
– Regularly back up your data to prevent loss.
– Ensure you have a recovery plan in place.
These practices will help maintain the security of your JSON API. Regular assessments can identify areas for improvement.
Real-world Examples of Secure JSON APIs
Examining successful implementations can provide valuable insights. Here are some notable examples:
1. Google APIs
– Google takes security seriously.
– It uses OAuth for user authentication.
2. Twitter API
– Twitter employs rate limiting & access tokens.
– This prevents abuse of their services.
3. GitHub API
– GitHub emphasizes secure API access.
– They issue personal access tokens for improved security.
These APIs illustrate effective measures for securing JSON APIs. They can serve as a model in your API development efforts.
- Implement OAuth for secure authentication.
- Use access tokens to limit API access.
- Regularly assess API security measures.
By learning from established examples, you can strengthen your JSON API security & functionality.
Conclusion on Creating a Secure JSON API for Spreadsheet Data
Creating a secure JSON API for your spreadsheet data requires careful planning. Each step in the process grows in importance as you build. By focusing on security, you protect sensitive information effectively.
Stay informed about new security practices. Apply them to your development process consistently. Engaging with the community can also provide insights. This will enhance both your knowledge & your API security.
<<<<< Buy Now from Official offer >>>>>

Feature of Sheet2DB
Sheet2DB provides a seamless experience for converting spreadsheet data into a JSON API. With features designed to streamline processes & increase efficiency, it stands out in the market. Users can unlock a lifetime access to the platform by redeeming codes within 60 days after purchase. Here are key features:
- Easy conversion of Google Sheets to JSON API, making data retrieval simple.
- Users can stack up to 4 codes for enhanced functionality.
- Access to all future updates under the Basic Plan.
- Compatible with various frameworks & languages.
- Secure API for data transfer, ensuring privacy & integrity.
Challenges of Sheet2DB
Despite its advantages, Sheet2DB comes with challenges. Users often report some limitations in features that affect its usability. For instance, the setup process can be complex for new users, leading to a steep learning curve. Feedback highlights difficulties with:
- Compatibility with older spreadsheet formats.
- Specific API configuration settings that require a technical background.
- Limited customer support, which can frustrate users seeking immediate assistance.
To mitigate these issues, users are encouraged to invest time in training modules & forums available online. Engaging with the community can also provide insights & solutions.
Price of Sheet2DB
Pricing for Sheet2DB remains competitive. The product offers several plans to accommodate different needs. Here’s a breakdown of the pricing structure:
| Plan | Price |
|---|---|
| Plan 1 | $59 |
| Plan 2 | $118 |
| Plan 3 | $177 |
The plans cater to individuals & businesses alike, depending on their usage requirements. Choosing the right plan can enhance the return on investment.
Limitations Sheet2DB
While Sheet2DB offers many advantages, some limitations exist. Users have noted certain features are missing, which may hinder performance. Highlights of these limitations include:
- Lack of advanced authentication methods for API access.
- Limited data formats, restricting how users can manipulate their output.
- Inflexibility in customization for visual layouts & data representation.
Addressing these gaps may involve integrating third-party tools or adapting current workflows. Continuous improvement in user feedback loops could enhance future iterations of the platform.
Case Studies
Real-life examples showcase how Sheet2DB has been successfully employed across various sectors. One notable case involved a nonprofit organization that utilized the platform for real-time data updates relevant to fund allocation. The organization benefited from:
- Improved data accessibility for team members & stakeholders.
- Enhanced efficiency, reducing the time taken to update databases from hours to minutes.
- Increased trust among donors due to transparent data handling.
Another case study featured a startup using Sheet2DB for customer feedback collection. Their results included:
- Streamlined processes that minimized user friction.
- Effective analysis of customer responses through organized JSON outputs.
- Increased engagement through quicker response times to customer queries.
Recommendations for Sheet2DB
To maximize the benefits of Sheet2DB, users should consider several actionable strategies. These tips can enhance overall performance & user experience:
- Invest in tutorials to familiarize yourself with the platform.
- Utilize forums to exchange knowledge with other users.
- Combine Sheet2DB with automation tools for better workflow integration.
- Regularly review updates to stay current with new features.
- Conduct tests on different data sets to understand the application limits.
By leveraging these strategies, users can improve their efficiency & get the most out of their subscription.
Key Functionalities of JSON API Creation
Creating a secure JSON API for spreadsheet data through Sheet2DB involves several crucial functionalities. Understanding these can enhance data management:
- API Key Generation for secure access.
- User authentication to ensure data privacy.
- Data transformation capabilities to suit various applications.
- Integration with existing applications for seamless functionality.
- Version control for API management, ensuring stability.
Best Practices for API Security
Ensuring security is vital when working with JSON APIs. Here are key best practices to adopt:
- Use HTTPS to encrypt data in transit.
- Implement API keys & secrets for sensitive endpoints.
- Regularly rotate keys to minimize exposure risks.
- Monitor API usage for unusual patterns.
- Maintain updated documentation on security procedures.
Following these practices can significantly enhance the security of your API & protect your data from unauthorized access.
Advanced Usage Strategies
Maximizing the use of Sheet2DB often requires advanced strategies. Consider experimenting with these approaches:
- Create multiple endpoints to segregate data based on use case.
- Leverage webhooks for real-time data updates.
- Utilize caching mechanisms to enhance performance.
- Test extensively before deploying changes to the API.
- Document all changes clearly to improve team collaboration.
Integration of Third-party Tools
Integrating third-party tools can enhance the functionality of Sheet2DB. Here are a few tools that work well:
- Zapier for workflow automation.
- Postman for API testing & documentation.
- Google Data Studio for visual data representation.
- Slack for team notifications on API updates.
- Amazon S3 for secure data storage.
Using these tools together can elevate your experience & streamline processes.
Feedback & Evolution
User feedback has driven many changes in Sheet2DB. Listening to users’ needs can guide future developments. Collecting input regarding:
- Feature requests for enhanced functionalities.
- UI/UX improvements for better accessibility.
- Support responses to facilitate quicker resolutions.
Companies often thrive when they prioritize user interactions. Adapting based on constructive feedback can foster a loyal customer base.
Monitoring & Optimization
Monitoring the performance of your Sheet2DB JSON API is crucial. Essential metrics to consider include:
- API response times for user satisfaction.
- Data fetch rates to gauge performance.
- Error rates to identify & rectify issues.
- User analytics to understand engagement levels.
- Security logs to monitor unauthorized attempts.
Analyzing these metrics will inform necessary optimizations to improve API functionality.
Conclusion
Building a secure JSON API for spreadsheet data using Sheet2DB can greatly enhance data management efficiency. Applying recommended practices & tools will further optimize this process. Continuous improvement through evaluation & user feedback ensures that the API remains relevant & effective for its users’ needs.
What are the basic steps to create a secure JSON API for spreadsheet data?
To create a secure JSON API for your spreadsheet data, you should start by defining the data structure & establishing an API endpoint. Next, implement authentication methods such as OAuth or API keys. Ensure to use HTTPS to encrypt the data during transmission. Finally, validate inputs & set permissions for data access.
How can I secure the API endpoint?
Securing the API endpoint involves limiting access using authentication & authorization mechanisms. And another thing, you can implement rate limiting to mitigate abuse & use firewall rules to restrict IP addresses that can access the API.
What authentication methods are recommended for a secure API?
Popular methods for securing an API include using OAuth for token-based authentication & API keys for straightforward access management. You may also consider using JWT (JSON Web Tokens) for stateless authentication.
Why is HTTPS important for my JSON API?
Using HTTPS is crucial because it encrypts the data in transit, protecting it from interception by third parties. This ensures that sensitive information exchanged through the API remains confidential.
How can I validate inputs to enhance security?
Input validation can be enhanced by implementing data type checks, ensuring that the data meets expected formats, & sanitizing inputs to prevent injection attacks. Always validate both client-side & server-side.
What is rate limiting & why is it necessary?
Rate limiting is a technique used to control the number of requests a user can make to the API in a given timeframe. This is necessary to prevent abuse & to ensure fair usage among all users, as well as to protect against denial-of-service attacks.
How can I manage permissions for data access?
Permissions for data access can be managed by defining roles & scopes in your application. Utilize access control lists (ACLs) to specify which users or applications can access specific data or API endpoints.
What are some common security threats to APIs?
Common security threats to APIs include data leakage, unauthorized access, injection attacks, & denial-of-service attacks. Awareness of these threats can help you implement better security measures.
How do I monitor the API for security vulnerabilities?
You can monitor an API for security vulnerabilities by implementing logging & monitoring tools that analyze access patterns, error rates, & unusual activity. Regular security audits & vulnerability assessments are also essential.
What role does documentation play in API security?
Proper documentation plays a vital role in API security by providing clear guidelines on how to use authentication methods, how to access endpoints securely, & detailing data formats. This helps developers understand how to interact safely with the API.
<<<<< Buy Now from Official offer >>>>>
Conclusion
Creating a secure JSON API for your spreadsheet data doesn’t have to be complicated. By following key steps like using strong authentication, validating inputs, & employing HTTPS, you can protect your data from unwanted access. Remember to regularly update your security measures & monitor for any suspicious activity. With these practices in place, you can ensure that your API remains safe while still being easy to use. So, go ahead & build that secure JSON API, & confidently share your spreadsheet data with the world!
<<<<< Buy Now from Official offer >>>>>